Data Hazard Detection and Handling – Part 1
Computer Architecture
Abstract
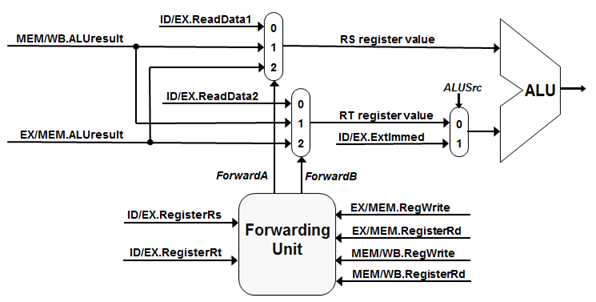
In this activity, students will learn how to use the first four MIPS data hazard detection rules to identity data hazards between MIPS R-type assembly instructions. They will discover how adding a Forwarding Unit to evaluate the rules, and two additional MUXes, to the MIPS pipelined datapath will allow cause forwarding of the modified data to handle detected data hazards. This activity was designed for use in a Computer Architecture course that incorporates the MIPS datapath.
After completing this activity, students should be able to:
- Use two data hazard detection rules to identify data hazards between MIPS R-type instructions that can be handled by forwarding data from the EX/MEM pipeline register.
- Use two data hazard detection rules to identify data hazards between MIPS R-type instructions that can be handled by forwarding data from the MEM/WB pipeline register.
- Detail the hardware units, along with their inputs and outputs, need to support the four data hazard detection rules within a MIPS pipelined datapath.
This activity was developed with NSF support through IUSE-1626765. You may request access to this activity via the following link: IntroCS-POGIL Activity Writing Program.
- Level: Undergraduate
- Setting: Classroom
- Activity Type: Learning Cycle
- Discipline: Computer Science
- Courses: Computer Architecture
- Keywords: data hazards, MIPS pipeline data hazards, data hazard detection, data hazard detection rules, forwarding unit
Downloads
Published
How to Cite
Issue
Section
License
Copyright of this work and the permissions granted to users of the PAC are defined in the PAC Activity User License.

